
While I was on my spring cleaning spree a few weeks ago, I unexpectedly found back a familiar SAO postcard sent by Taka. This wasn’t just any postcard; it was a remnant from a game launched by the official Sword Art Online anime account to celebrate the release of Alicization’s anime adaptation.
As of today the website for this game is no longer accessible, and not many people know about it, so I thought: “Why not write an article about it?”
Credits
Author: Celest
Special thanks: YSRKEN
, YamatoAl
, Raïto
【REVIEW】 SAO Decode - The mysterious Alicization riddle from 2018
The beginning
It all began with a thread of three tweets from the official Sword Art Online anime account on September 29, 2018. The tweets were as follows:
1/3
【仮想空間管理課より緊急連絡1/3】
こちら総務省の菊岡誠二郎!緊急事態だ!10/6より放送予定のSAOアニメ最新作の情報が何者かに奪われてしまった!
たった今、僕の部署からミッションが布告された。困難な仕事になるだろう…どうか力を貸してくれないか?!#SAO_DECODE
https://sao-alicization.net/special/sao_decode/index.html— アニメ ソードアート・オンライン 公式 (@sao_anime) September 29, 2018
Translation:
[Urgent Message from the Virtual Space Management Division 1/3]
This is Kikuoka Seijirou from the Ministry of Internal Affairs! We’ve got an emergency! Information about the latest SAO anime scheduled to air on September 6th has been stolen by an unidentified group!
Just now, a mission has been issued from my department. It’s going to be a tough job… but will you lend us your strength?! #SAO_DECODE
2/3
【仮想空間管理課より緊急連絡2/3】
現在も犯人からの敵対的なハッキングは続いている。だが僕も素人じゃない。防御情報を展開し時間を稼いでいるところさ。この隙に相手側のサーバを特定、データを抜き取って削除してほしい。いいか、くれぐれも削除してくれよ!#SAO_DECODE
https://sao-alicization.net/special/sao_decode/index.html— アニメ ソードアート・オンライン 公式 (@sao_anime) September 29, 2018
Translation:
[Urgent Message from the Virtual Space Management Division 2/3]
The hostile hacking from the culprit is still ongoing. But I’m no amateur either. I’ve deployed defensive protocols to buy us some time. While I can still hold out, I need you to identify the enemy’s server, extract the data, and delete it. Got it? Make sure you delete it!
#SAO_DECODE
3/3
【仮想空間管理課より緊急連絡3/3】
【サーバーログから、違和感のある部分を抜き出してある。これがきっと犯人につながる手がかりになるはずだ。知識なんかなくても大丈夫。知っていることを繋ぎ合わせれば必ず答えにたどり着けるはずだ!では諸君、健闘を祈る!#SAO_DECODE
https://sao-alicization.net/special/sao_decode/index.html— アニメ ソードアート・オンライン 公式 (@sao_anime) September 29, 2018
Translation:
[Urgent Message from the Virtual Space Management Division 3/3]
I’ve extracted the suspicious parts from the server logs. Its content will surely be a clue leading us to the culprit. you won’t be in need of technical knowledge. If you put together all the elements you have in possession, you will surely bound to reach the answer! Now then y’all, good luck! #SAO_DECODE
For now, let’s look at the image from the 3rd tweet. Those logs show us four requests made by the ip 123.456.789.xxx on the domain https://sao-decode.net.
This IP is a placeholder, so let’s look at the four requested URLs instead:
- https://sao-decode.net/01.html
- https://sao-decode.net/02.html
- https://sao-decode.net/ ■■■■■■■■■■■.html
- https://sao-decode.net/command.html
The third URL seems to be censored with exactly eleven squares.
Note that all the requests returned an error 500, which means there has been an Internal Server Error. So the hackers shouldn’t have received any content from Kikuoka’s servers other than this error…
Anyways, let’s go ahead and look at the first url.
The first enigma
By visiting https://sao-decode.net/01.html , we’re taken to a black, single-page website displaying the following image:

Here’s our first enigma.
Some might have guessed the answer was FORM by reading the letters linked to the selected colors, but it’s a little bit complicated than that:
Each letter of the response match the nth letter from the name of the SAO arc that is associated to the letter with the same colour of each number ; nth being the actual associated number.
So this means:
• 8th letter of Fairy dance: N
• 4th letter of Ordinal Scale: I
• 3rd letter of Phantom Bullet: N
• 5th letter of Mother’s Rosario: E
And there we have our answer: NINE.
Seeing as there aren’t any more clue, let’s head out to the second URL.
The second enigma
The page at https://sao-decode.net/02.html closely resembles the previous one, displaying the following image:

We’ve got here a puzzle containing all kind of characters, with the instructions to Read every ____ letters.
If we connect the dots, we can assume that this puzzle uses the first puzzle’s solution.
Now if only the creators of this puzzle knew that letters and special characters do NOT count as “letters”… Thankfully this puzzle isn’t that much hard to solve.
Anyways, if we read every nine letters characters starting with the first one, we obtain this string: 42813705736
This string of is 11-characters long, which actually corresponds to the lengh of the 3rd censored link, so let’s try accessing this page.
The third enigma
Accessing this page https://sao-decode.net/42813705736.html finally gives you this message from Kikuoka:
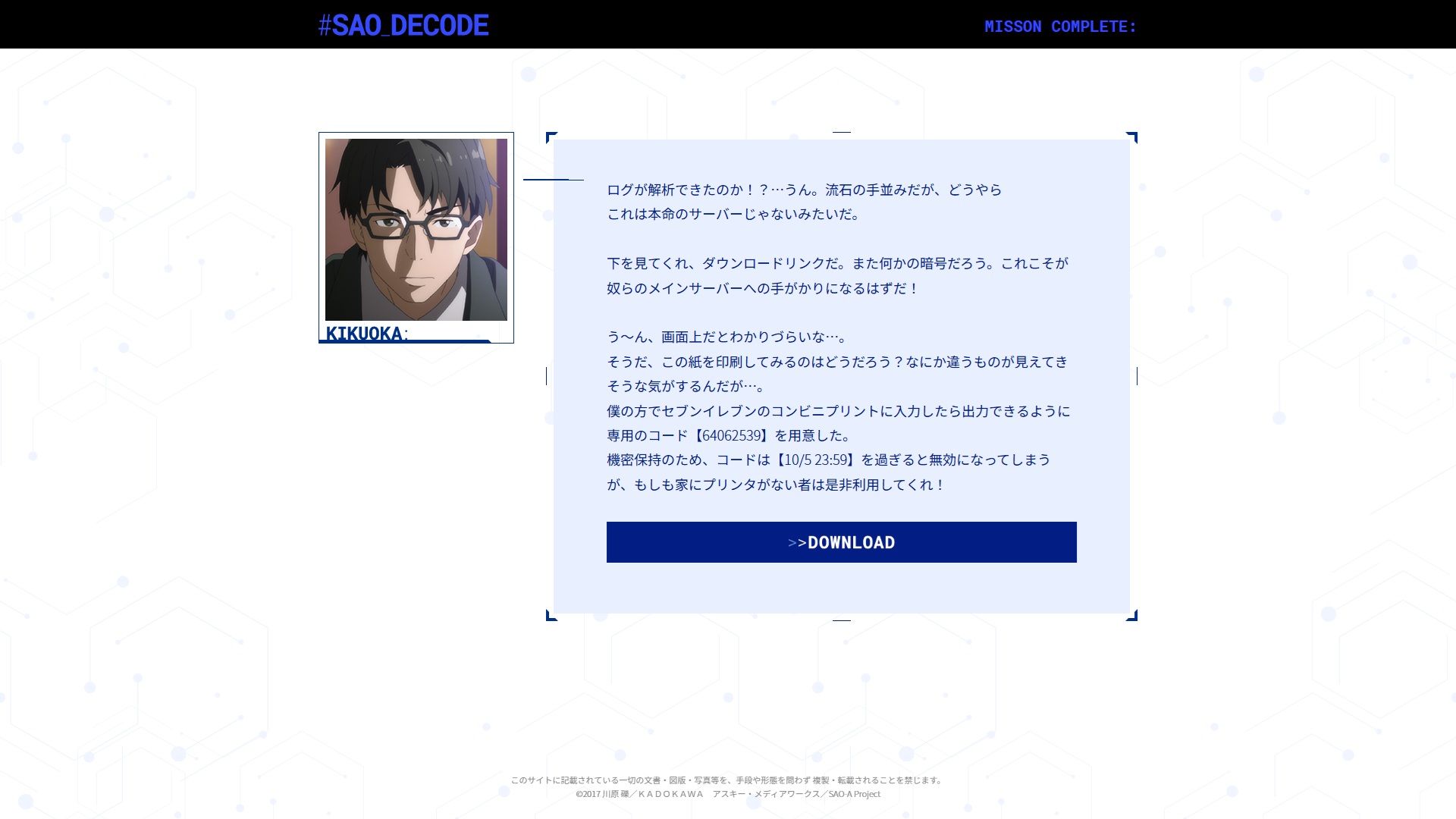
ログが解析できたのか!?…うん。流石の手並みだが、どうやら
これは本命のサーバーじゃないみたいだ。下を見てくれ、ダウンロードリンクだ。また何かの暗号だろう。これこそが奴らのメインサーバーへの手がかりになるはずだ!
う〜ん、画面上だとわかりづらいな…。
そうだ、この紙を印刷してみるのはどうだろう?なにか違うものが見えてきそうな気がするんだが…。
僕の方でセブンイレブンのコンビニプリントに入力したら出力できるように専用のコード【64062539】を用意した。
機密保持のため、コードは【10/5 23:59】を過ぎると無効になってしまうが、もしも家にプリンタがない者は是非利用してくれ!
Translation:
So did you get to analyze the logs!? … Yeah. As expected, excellent work.
But looks like this isn’t their main server.
Look below, there’s a download link. this is surely yet another cipher. I’m sure this is the clue that can lead us to their main server!
Hmmmm, it’s kind-of hard to understand anything on a screen…
What if we check this out on paper? I’ve got a feeling something different might become visible.
Here, use this code 【64062539】 to print this puzzle with special printers from SevenEleven konbinis.
The code will expire after October 5th at 23:59 out of confidentiality, so if you don’t have a printer where you live, don’t hesitate to use the code!
The DOWNLOAD button give you access to a pdf with this content:
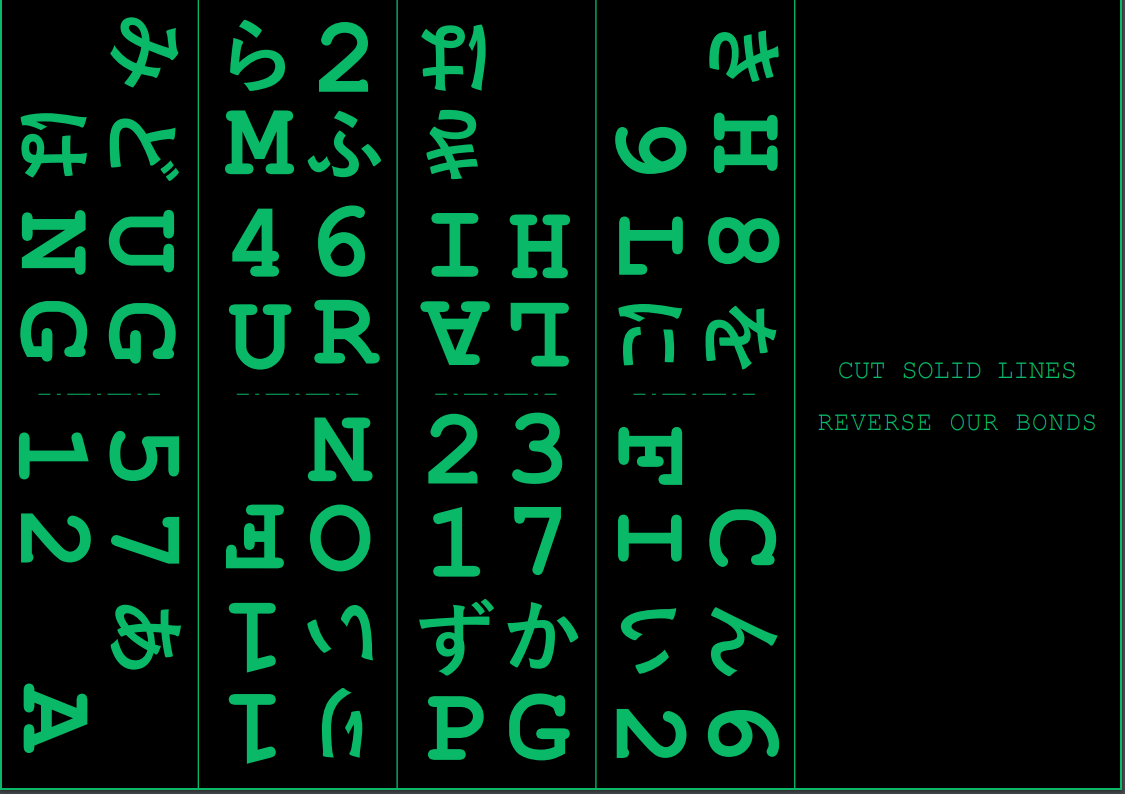
This puzzle is a bit tricky, but still fairly straightforward once you notice one key word: LAUGHING COFFIN. I’ll explain why in just a moment.
Printing the puzzle is actually very helpful, as you won’t be able to fully grasp the trick without physically cutting the paper strips and folding them in half.
The solution involves folding each strip of paper and looking at the character that appears on the opposite side of each letter in “LAUGHING COFFIN.”

By translating LAUGHING COFFIN in that way, we get 57231217468をURLに, which means “(add) 57231217468 to your URL”.
A puzzle harder than it looks like
Here we are on the https://sao-decode.net/57231217468.html page.
This one gives us access to a console with a field accepting inputs.
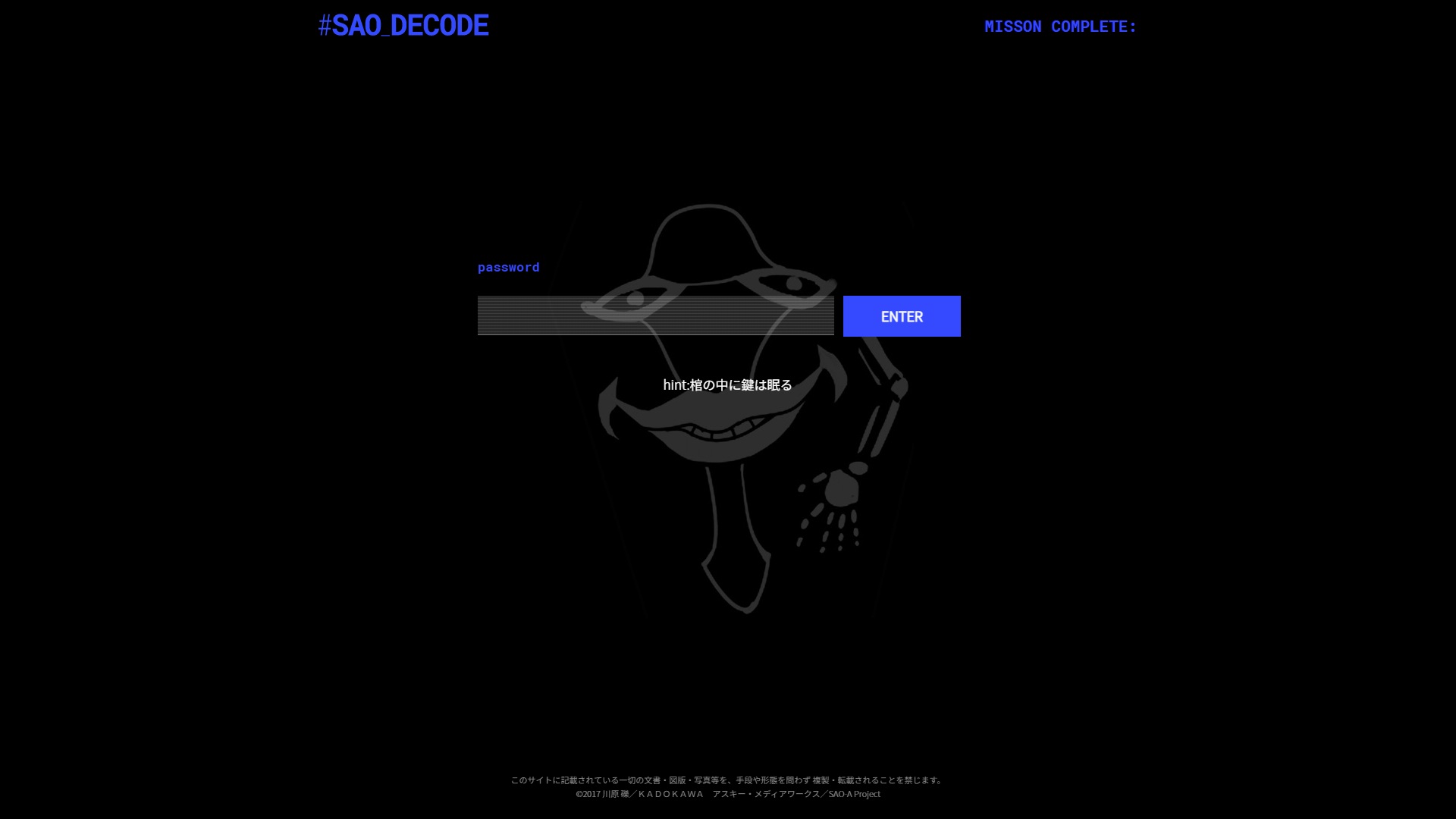
If you tried to input anything other than what the console expects, the message >無効なパスワードです (Invalid password) shows up.
Anyway, the only hint this page gives us is: 棺の中に鍵は眠る (“The key sleeps inside the Coffin”). Even with context from the series, it doesn’t offer much to go on.
We might have overlooked some clues in the previous puzzle, so let’s go back and take another look.
The fact that there was unused hiragana characters on the pdf is really suspicious…
If you arrange the paper strips into a spiral that forms the phrase “LAUGHING COFFIN”, then unfold the inner sections of the spiral, you’ll uncover the following words:
• みどり1 (Green 1)
• はい1 (Gray 1)
• きん6 (Gold 6)
• はい2 (Gray 2)
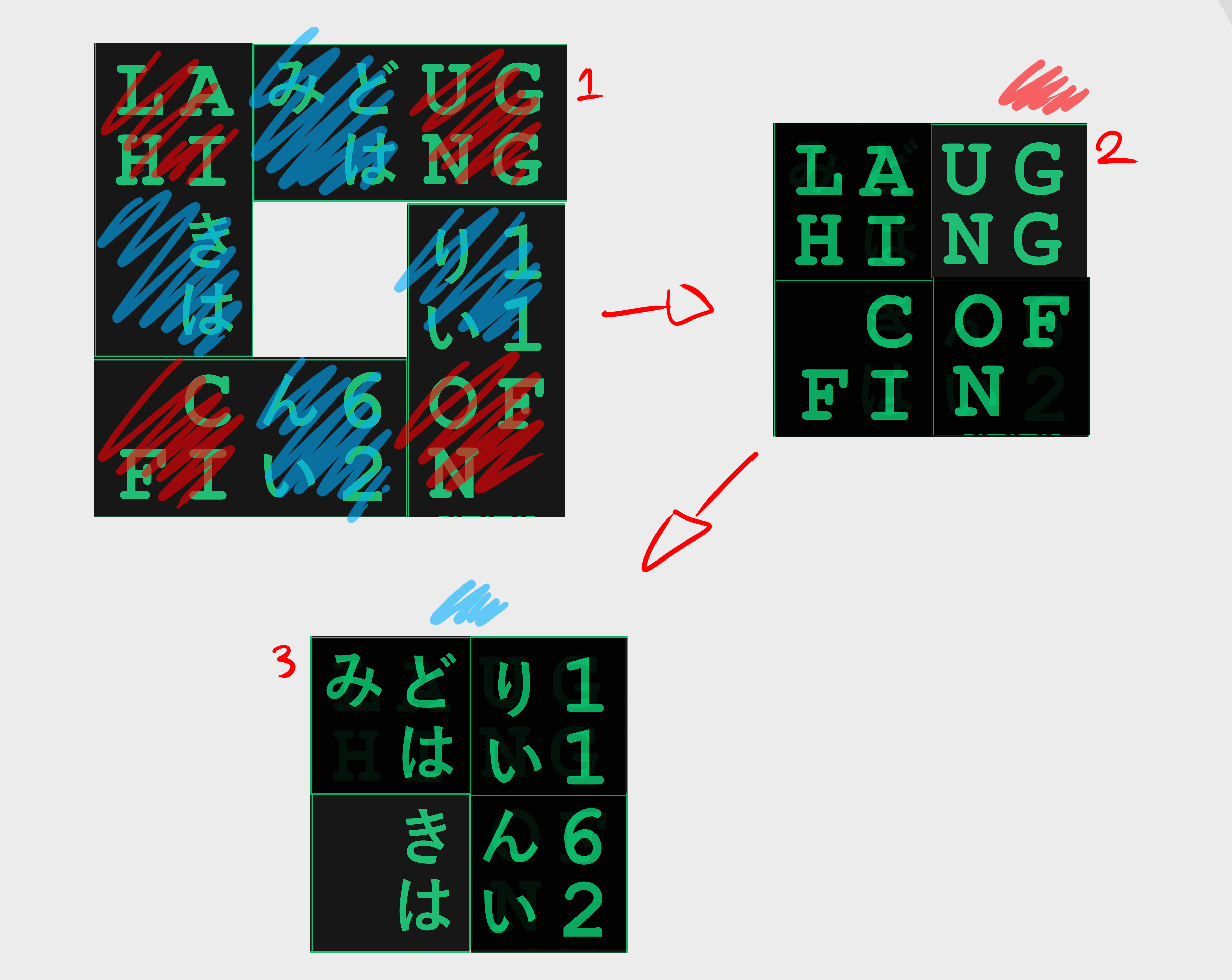
The colours scheme pretty much has something to do with the first puzzle, so if we go back to it and get the letter of each arc corresponding to the colours given above, as well as the position, we get FOUR:
• 1st letter of Fairy dance (green): F
• 1st letter of Ordinal Scale (Gray): O
• 6th letter of Calibur: N
• 2nd letter of Ordinal Scale (Gray): R
And just like with NINE, if we write down every 4th characters of the second puzzle (starting with the first one…), we obtain this formula 480+251+(37*7)+89-72=PASS, which results to 1007 ; Kirito’s birthdate, the one the PKers want inside a coffin.
This password was also hardcoded locally inside the JS code of the page, so another way to login was to deobfuscate the code and reverse engineer it.
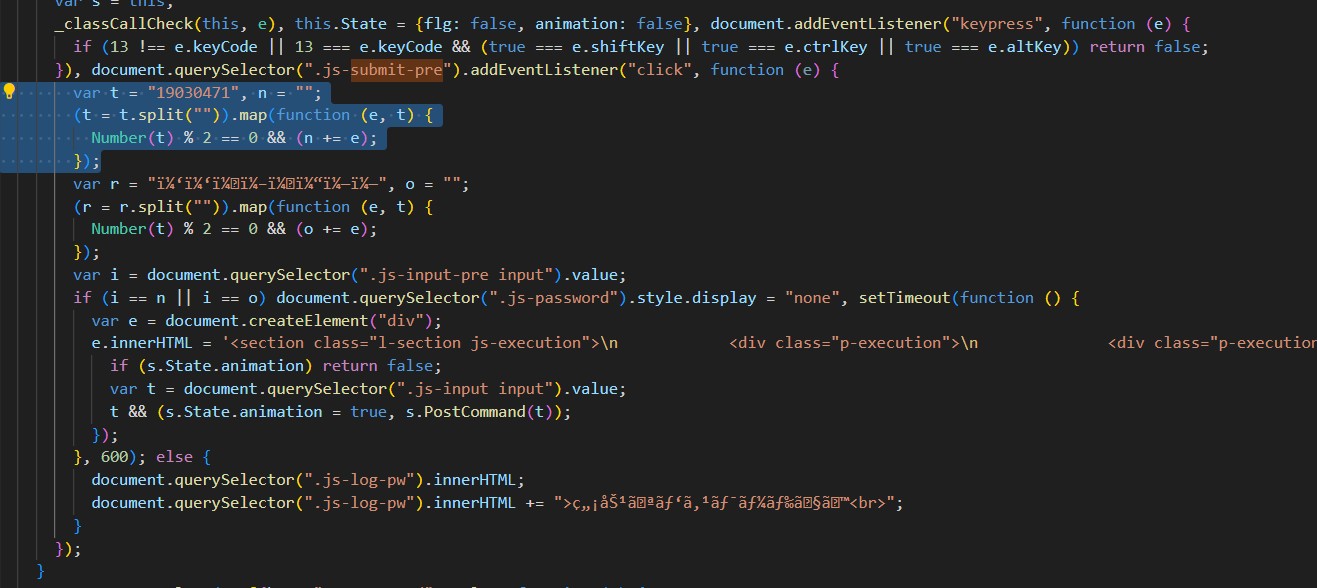
The chunk of code selected above simply selected every 2n numbers of the string 19030471, which results to 1007 (another part of the code made 1007 valid, mostly to support japanese full-width characters)
Note: The console requests made after entering the right password was handled by a proper API. This API was taken down a few months after sao-decode.net was revealed, so no one can use the page as of today, even with the wayback machine.
Now that we’re logged in, let’s go back and look at the fourth original page for the CMD’s documentation : https://sao-decode.net/command.html
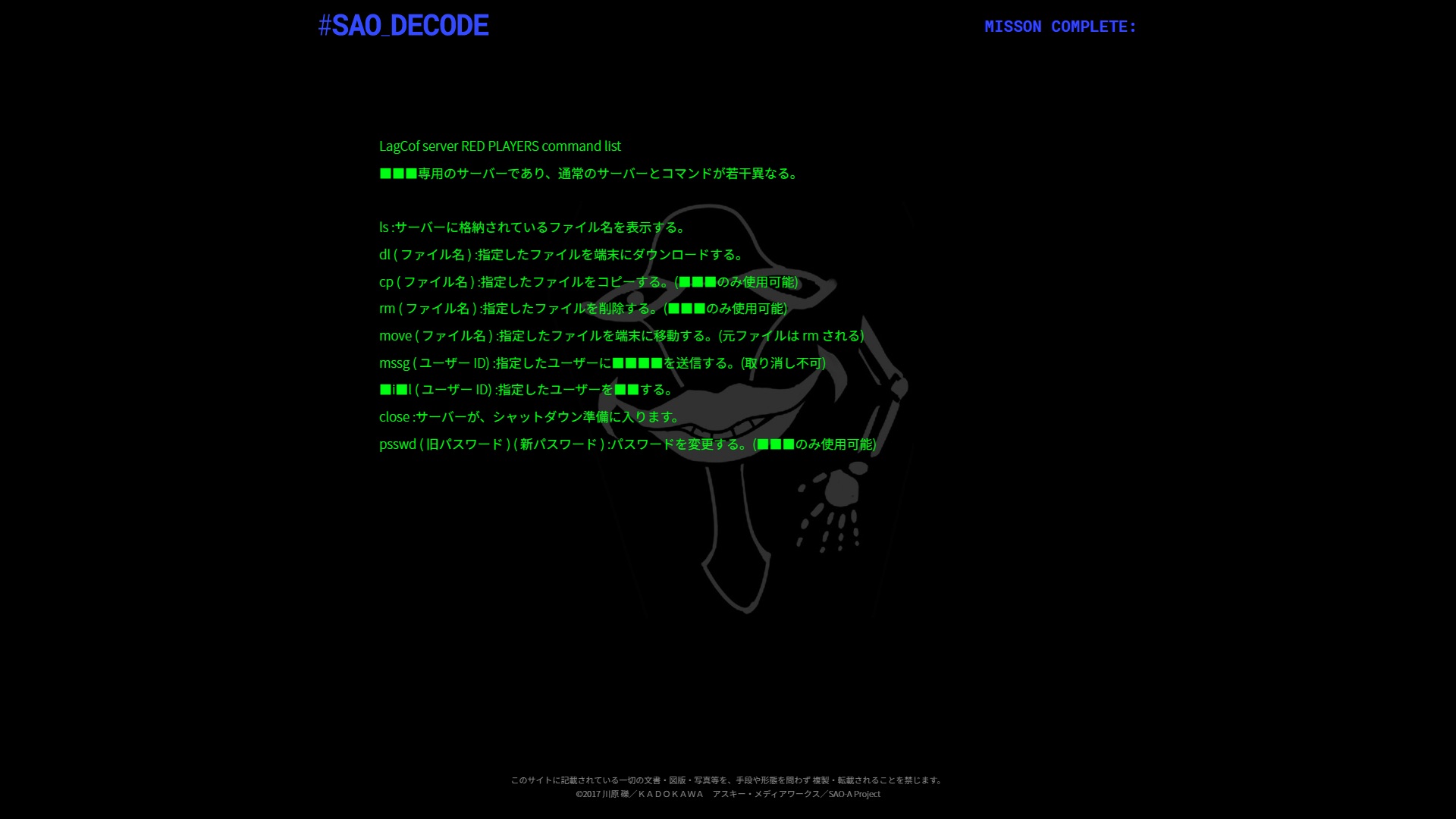
LagCof server RED PLAYERS command list
■■■専用のサーバーであり、通常のサーバーとコマンドが若干異なる。ls :サーバーに格納されているファイル名を表示する。
dl ( ファイル名 ) :指定したファイルを端末にダウンロードする。
cp ( ファイル名 ) :指定したファイルをコピーする。(■■■のみ使用可能)
rm ( ファイル名 ) :指定したファイルを削除する。(■■■のみ使用可能)
move ( ファイル名 ) :指定したファイルを端末に移動する。(元ファイルは rm される)
mssg ( ユーザー ID) :指定したユーザーに■■■■を送信する。(取り消し不可)
■i■l ( ユーザー ID) :指定したユーザーを■■する。
close :サーバーが、シャットダウン準備に入ります。
psswd ( 旧パスワード ) ( 新パスワード ) :パスワードを変更する。(■■■のみ使用可能)
Translation:
LagCof server RED PLAYERS command list
■■■’s dedicated server; the commands are slightly different from those of a regular server.
• ls : Displays all the filenames stored on the server. (Celest’s note: should’ve been “current dir” instead of “server”)
• dl (filename) : Downloads specified file to the terminal.
• cp (filename) : Copies specified file. (Only usable by ■■■)
• rm (filename) : Deletes specified file. (Only usable by ■■■)
• move (filename) : Moves specified file to the terminal. (Original file will be rm’d)
• mssg (user ID) : Sends ■■■■ to specified user. (Cannot be undone)
• ■i■l (user ID) : ■■ specified user.
• close : The server will shutdown.
• psswd (old password) (new password) : Changes password. (Only usable by ■■■)
Spoilers: ■i■l is “kill”, ■■■ is “PoH”, ■■■■ is “mail”.
Our final experimentation can now begin.
Kikuoka’s final task
With the API now unavailable, this is the most challenging part of the article to write. I’ll be relying on various screenshots I managed to find on Discord, as well as my memory.
You could do quite a bit with the CMD, like sending messages to PoH, adding someone to be “killed,” and so on. But that’s not really the focus here.
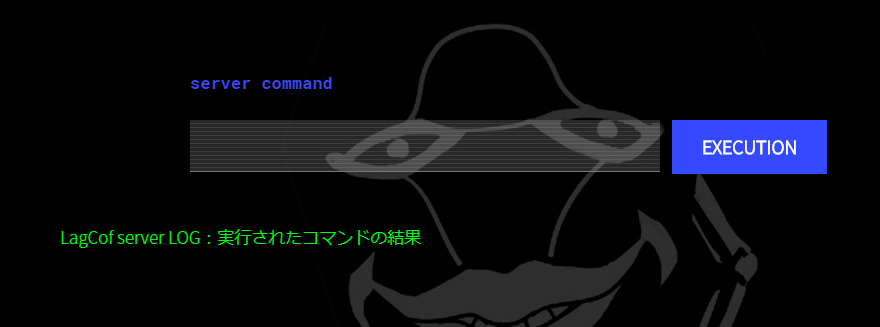
- The wrong ending
ls
>91284732556.pdf
dl 91284732556.pdf
Those two commands allows you to 1. list the files inside the main directory of LagCof server LOG, and 2. download the only listed file 91284732556.pdf. This would take you to a congratulation page with a message from Kikuoka:
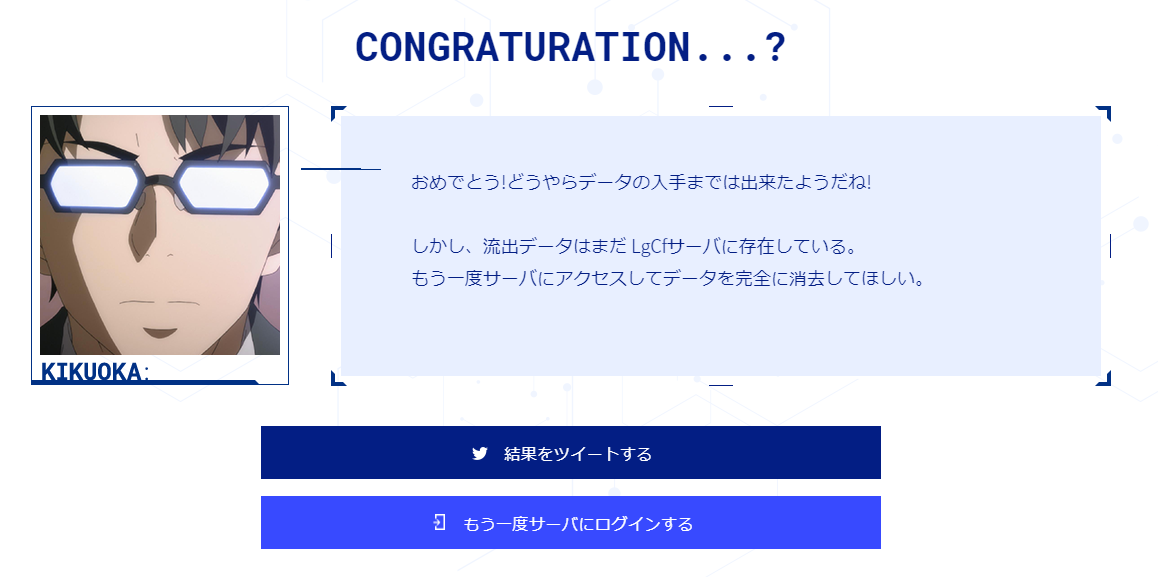
Translation:
Congrats! Looks like you managed to download the data!
Though the leaked data still exists on their server. Please access their server again and delete it.
- The good ending
Since rm 91284732556.pdf can only be used by Po– er, I mean ■■■, we have no choice but to remove the pdf using move 91284732556.pdf. This leads us to the good ending:

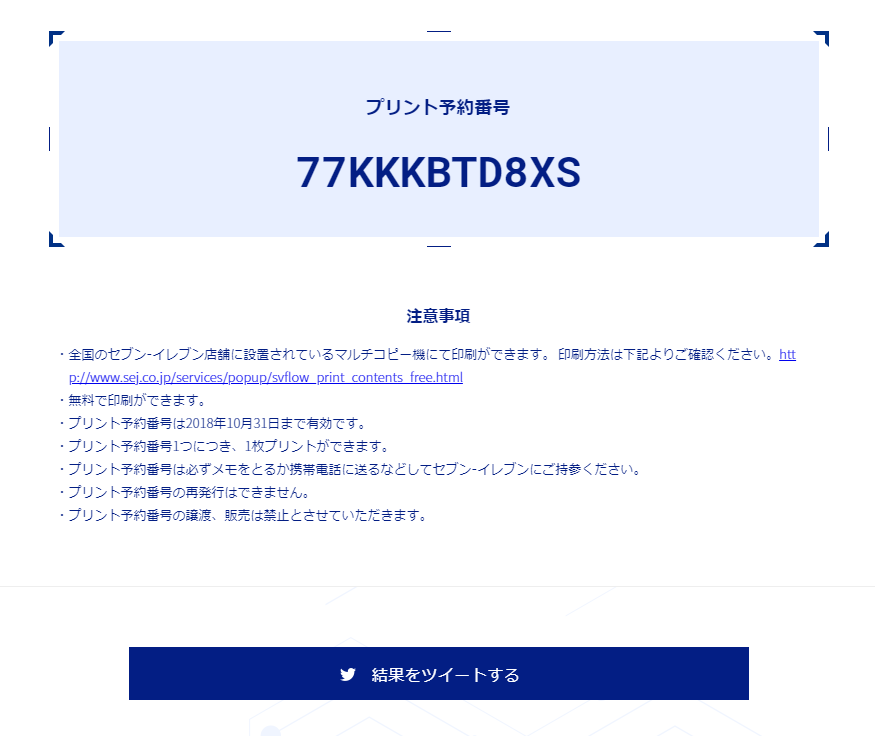

Translation:
Congratulations!
You’re the XXth person to solve this game!
I just confirmed that the leaked data from the LgCf server has been deleted!
Thank you! Now we should be able to make it safely to October 6th without leaks!
Though, the Laughing Coffin huh… Looks like Kirito-kun’s path won’t be an easy one…
Well, no time for gloomy thoughts now! First things first, congrats on clearing the game!
As always, I’ve uploaded the data you retrieved to the special printers from the konbinis!
You’ll find the code that’ll allow you to print your prize below, so feel free to print it out and enjoy it.
I’m serious, thank you!
Note: The clear page was unique to the clearers and no one managed to archive the page. Above was shown screenshots from various users.
Looking at the screenshots I sent to Raïto back in 2018, it looks like I was the 300th person to solve the game. Not bad, 16-years-old me!
Rewards
- Special postcard
Taka went to a konbini and printed mine and Raïto’s postcard to ship it to me while she was still in japan, Here’s how it looked like:
Finally received my and my friend’s postal cards of the SAO decode game, thank you so much @Takargo ^-^
— Celest (@_xCelest) Oct 22, 2018
- Character design images
The page also allowed us to download three images of the Rulid trio.


